NEW YORK -- Dozens of countries were hit with a cyberattack Friday that locked up computers and held users' files for ransom at hospitals, companies and government agencies.
The attack appeared to exploit a vulnerability that was purportedly identified by the U.S. National Security Agency for its own intelligence-gathering purposes and was later leaked on the Internet.
The United Kingdom's National Health Service was hit hard, its hospitals forced to close wards and emergency rooms. Spain, Portugal and Russia also were struck. Several cybersecurity firms said they had identified the malicious software behind the attack in more than 60 countries, with Russia apparently the hardest-hit.
Kaspersky Lab, a Russian cybersecurity firm, said it had recorded at least 45,000 attacks in as many as 74 countries, including the U.S., where its effects seemed muted. In addition to Russia, the biggest targets appeared to be Ukraine and India, nations where it is common to find older versions of the Windows operating system in use.
The Russian Interior Ministry confirmed it was among those that fell victim to the "ransomware" -- software that locks up a computer and typically flashes a message demanding payment to release the user's data.
Mikko Hypponen, chief research officer at Helsinki-based cybersecurity company F-Secure, called it "the biggest ransomware outbreak in history."
It was not immediately clear who was behind the attacks, but the acts deeply alarmed cybersecurity experts and underscored the enormous vulnerabilities to Internet invasions faced by disjointed networks of computer systems around the world.
Chris Wysopal of the software security firm Veracode said criminal organizations probably were behind the attack, given how quickly the malware spread.
"For so many organizations in the same day to be hit, this is unprecedented," Wysopal said.
"When people ask what keeps you up at night, it's this," said Chris Camacho, chief strategy officer at Flashpoint, a New York security firm tracking the attacks.
Security experts said the attack appeared to be caused by a self-replicating piece of software, known as WannaCry, that takes advantages of vulnerabilities in older versions of Microsoft Windows. It spreads from computer to computer by email as it finds exposed targets. Targets were sent an encrypted, compressed file that, once loaded, allowed the ransomware to infiltrate the quarry's systems.
Its ransom demands start at $300 and increase after two hours to $400, $500 and then $600, said Kurt Baumgartner, a security researcher at Kaspersky Lab.
The security holes it exploits were disclosed several weeks ago by TheShadowBrokers, a mysterious group that has repeatedly published what it says are hacking tools used by the National Secury Agency as part of its intelligence-gathering.
Shortly after that disclosure, Microsoft announced in March that it had already issued software "patches" for those holes. But many companies and individuals haven't installed the fixes yet or are using older versions of Windows that Microsoft no longer supports and didn't fix.
Experts said the malware enters companies and organizations when employees click on email attachments, then spreads quickly internally when employees share documents and other files.
Until organizations use the Microsoft patch, Camacho said, they could continue to be hit -- not just by ransomware, but by all kinds of malicious tools that can manipulate, steal or delete their data.
"There is going to be a lot more of these attacks," he said. "We'll see copycats, and not just for ransomware, but other attacks."
warning too late in U.K.
Reuters reported that employees of the U.K.'s National Health Service had been warned about the ransomware threat earlier Friday.
But by then it was already too late. As the disruptions rippled through at least 36 hospitals, doctors' offices and ambulance companies across the U.K., the health service declared the attack a "major incident," a warning that health services could be overwhelmed.
Many hospitals canceled all routine procedures and asked patients not to go to the hospital unless there was an emergency. Doctors' practices and pharmacies reported similar problems.
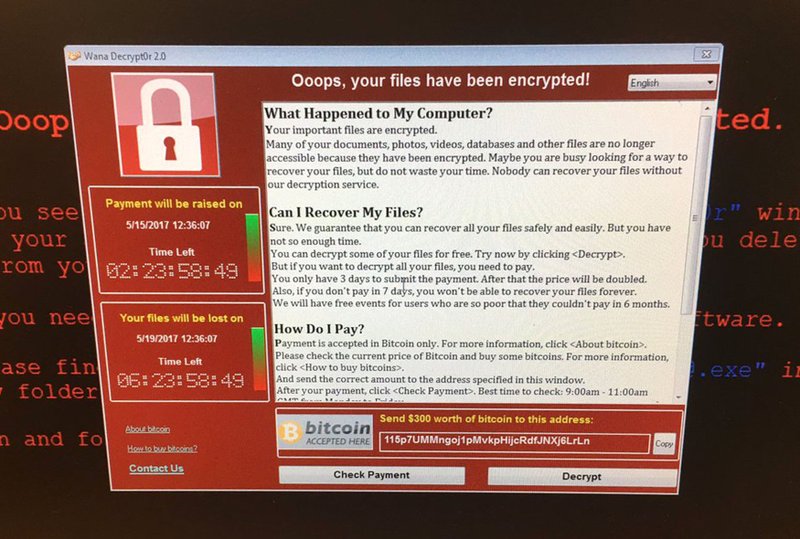
On social media, several images circulated Friday showing computer screens bearing a message that the user could not enter without first paying a $300 ransom in Bitcoin. One screenshot shows a countdown clock that appears to have begun with three full days.
"Can I recover my files?" the message asks. "Sure. We guarantee that you can recover all your files safely and easily."
Then it adds in slightly mangled syntax: "But you have not so enough time." It warns that the ransom demand will double after three days and that after seven days, "you won't be able to recover your files forever."
Many doctors reported that they could not retrieve their patients' files. It was unclear whether any of the targeted users paid the ransom.
NHS Digital, the National Health Service's information technology unit, said it would be working with Britain's National Cyber Security Center in efforts to resolve the failure. The attack, meanwhile, may have broader implications beyond Britain's health service.
"This attack was not specifically targeted at the [National Health Service] and is affecting organizations from across a range of sectors," NHS Digital said in its statement without giving details.
Nigel Inkster, former director of operations and intelligence for MI6, told Sky News that one of the reasons the National Health Service in particular was vulnerable was its outdated software system.
"A lot of hospital trusts in the U.K. -- 40-plus last time I checked -- are running their systems on Windows XP software, which hasn't been supported by Microsoft for two or three years," he said. "In other words, Microsoft is no longer looking for and seeking to repair vulnerabilities in the system."
Krishna Chinthapalli, a doctor at the U.K.'s National Hospital for Neurology and Neurosurgery who wrote a paper on cybersecurity for the British Medical Journal, said the National Health Service has been stuck with outdated software as government funding for the health service has been squeezed, "[Information technology] budgets are often one of the first ones to be reduced."
"Looking at the trends, it was going to happen," he said. "I did not expect an attack on this scale. That was a shock."
British Prime Minister Theresa May said there was no evidence patient data had been compromised and added that the attack had not specifically targeted the National Health Service.
"It's an international attack and a number of countries and organizations have been affected," she said.
The British health secretary, Jeremy Hunt, was briefed by cybersecurity experts.
Doctors were using pen and paper as the National Health Service struggled to get computers back online. Routine appointments were being canceled.
Patrick Ward, a 47-year-old sales director, said his heart operation, scheduled for Friday, was canceled at St. Bartholomew's Hospital in London.
Tom Griffiths, who was at the hospital for chemotherapy, said several cancer patients had to be sent home because their records or blood work couldn't be accessed.
"Both staff and patients were frankly pretty appalled that somebody, whoever they are, for commercial gain or otherwise, would attack a health care organization," he said. "It's stressful enough for someone going through recovery or treatment for cancer."
Spain, Portugal targets
Less was known about the scope of the attacks in Spain and Portugal, which affected companies like Telefonica, a global broadband and telecommunications company.
Spain's national cryptology center said it was dealing with "a massive ransomware attack" affecting Windows systems used by various organizations, without naming them.
Spain took steps to protect critical infrastructure in response to the attack. The government said it was communicating with more than 100 energy, transportation, telecommunications and financial services providers about the attack.
Spain's Industry Ministry said in a separate statement that the attack had not affected networks or customers using services offered by the companies targeted. Telefonica also indicated that the attack had targeted its internal network rather than its millions of customers. On Twitter, Chema Alonso, Telefonica's chief data officer, called initial news reports "exaggerated."
Later on Friday, Portugal reported attacks. Carlos Cabreiro, director of a police unit that fights cybercrime, told the newspaper Publico that the country was facing "computer attacks on a large scale against different Portuguese companies, especially communication operators."
Several employees of MegaFon, one of the largest cellphone operators in Russia, said its systems had been attacked Friday by malware like that used against the British health service, the news website Meduza.io reported.
Ransomware attacks are on the rise around the world. In 2016, Hollywood Presbyterian Medical Center in California said it had paid a $17,000 ransom to regain control of its computers from hackers.
Information for this article was contributed by Anick Jesdanun, Jill Lawless and Aritz Parra of The Associated Press; by Dan Bilefsky and Nicole Perlroth of The New York Times; and by Craig Timberg, Griff Witte and Karla Adam of The Washington Post.
A Section on 05/13/2017