LONDON -- The number of victims from last week's ransomware attack is expected to increase today as Asian workers who had logged off computers before Friday's strike, which has affected 150 countries, sign back on.
The components of the global cyberattack that seized hundreds of thousands of computer systems may be more complex than originally believed, an official in President Donald Trump's administration official said Sunday, and experts warned that the effects of the malicious software could linger for some time.
As a loose global network of cybersecurity experts fought a rear-guard battle against ransomware hackers, officials and experts on Sunday urged organizations and companies to update operating systems immediately to ensure they aren't vulnerable to a second, more powerful version of the software -- or to future versions that can't be stopped.
The initial attack, known as "WannaCry," paralyzed computers that run Britain's hospital network, Germany's national railway and scores of other companies and government agencies worldwide in what was believed to be the biggest online extortion scheme ever recorded.
The attack is more complicated because "the experts tell us that this code was cobbled together from many places and sources," according to an administration official who insisted on anonymity to discuss the government's cybersecurity plans. The more potential sources of the malicious code, the harder it is for investigators to run down the trail of possible perpetrators.
The source of the attack is a delicate issue for the United States because the vulnerability on which the malicious software is based was published by a group called the Shadow Brokers, which began publishing cybertools developed by the National Security Agency last summer.
Government investigators, while not publicly acknowledging that the computer code was developed by U.S. intelligence agencies as part of the country's growing arsenal of cyberweapons, say they are still investigating how the code got out.
At least two variants of the rapidly replicating worm were discovered Sunday and one did not include the so-called kill switch that allowed researchers to interrupt its spread Friday by diverting it to a dead end on the Internet.
Ryan Kalember, senior vice president at Proofpoint Inc., which helped stop its spread, said the version without a kill switch was able to spread but was benign because it contained a flaw that wouldn't allow it to take over a computer and demand ransom to unlock files. However, he said it's only a matter of time before a malevolent version exists.
"I still expect another to pop up and be fully operational," Kalember said. "We haven't fully dodged this bullet at all until we're patched against the vulnerability itself."
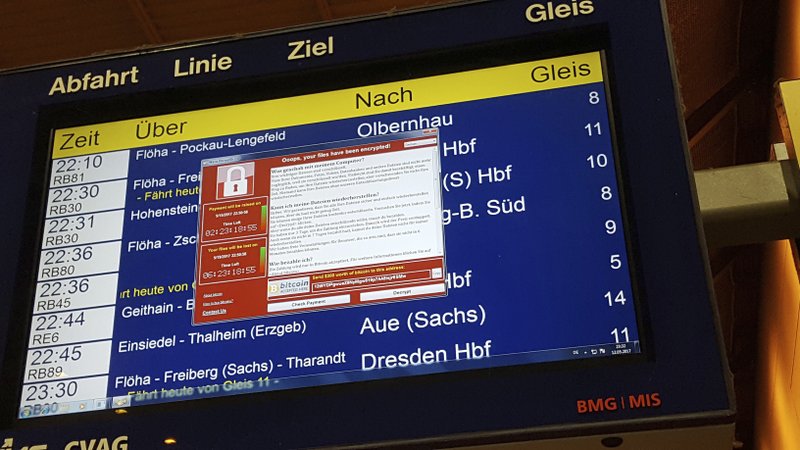
The attack held users hostage by freezing their computers, popping up a red screen with the words, "Oops, your files have been encrypted!" and demanding money through online bitcoin payment -- $300 at first, rising to $600 before it destroys files hours later.
It hit 200,000 victims across the world since Friday and is seen as an "escalating threat," said Rob Wainwright, the head of Europol, Europe's policing agency.
"The numbers are still going up," Wainwright said. "We've seen that the slowdown of the infection rate over Friday night, after a temporary fix around it, has now been overcome by a second variation the criminals have released."
"We've seen the rise of ransomware becoming the principal threat, I think, but this is something we haven't seen before -- the global reach is unprecedented," Wainwright said.
The malware affected the U.K.'s National Health Service, Russia's Ministry of Interior, Germany's Deutsche Bahn rail system, automakers Nissan Motor Co. and Renault SA, logistics giant FedEx Corp., and other company and hospital computer systems in countries from eastern Europe to the United States and Asia.
The hackers used the tool to encrypt files within affected computers, making them inaccessible, and demanded ransom -- typically $300 in bitcoin. Russia and Ukraine had a heavy concentration of infections, according to Dutch security company Avast Software BV.
Chinese media reported Sunday that students at several universities were hit, blocking access to their thesis papers and dissertation presentations.
Many workers, particularly in Asia, had logged off on Friday before the malicious software began proliferating across computer systems around the world. So the true effect of the attack is expected to emerge today as employees return and log in.
"It's this constant battle," said Ryan O'Leary, vice president of WhiteHat Security's threat research center. "The bad guys are always one step ahead."
It was too early to say who was behind the onslaught, which struck 100,000 organizations, and what their motivation was, aside from the obvious demand for money. So far, not many people have paid the ransom demanded by the malware, Europol spokesman Jan Op Gen Oorth said.
Researchers who helped prevent the spread of the malware and cybersecurity firms worked around the clock during the weekend to monitor the situation and install a software patch to block the worm from infecting computers in corporations across the U.S., Europe and Asia.
"Right now, just about every [information technology] department has been working all weekend rolling this out," Dan Wire, spokesman at Fireeye Security, said.
Businesses, government agencies and other organizations were urged to quickly implement a patch released by Microsoft Corp. The ransomware exploits older versions of Microsoft's operating system software, such as Windows XP.
Installing the patch is one way to secure computers against the virus. The other is to disable a type of software that connects computers to printers and faxes, which the virus exploits, O'Leary added.
Microsoft distributed a patch two months ago that could have forestalled much of the attack, but in many organizations it was likely lost among the blizzard of updates and patches that large corporations and governments strain to manage.
"It's one of those things, in a perfect world, if people were up to date on the patches, this wouldn't be a problem," O'Leary said. "But there are so many things to patch. The patch lists can be ginormous. It can be tough to tell which patch is important, until it is too late."
Microsoft Corp. President Brad Smith, in a blog post Sunday, said the attack is a "wake-up call" for governments in the U.S. and elsewhere to stop stockpiling tools to exploit digital vulnerabilities. "They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world," he said.
Microsoft said in a blog post Saturday that it was taking the "highly unusual" step of providing the patch for older versions of Windows it was otherwise no longer supporting, including Windows XP and Windows Server 2003.
While the scale of the attack shows Microsoft needs to strengthen its own capabilities, "there is simply no way for customers to protect themselves against threats unless they update their system," Smith said in his blog post.
"Otherwise they're literally fighting the problems of the present with tools from the past.
"This attack is a powerful reminder that information technology basics like keeping computers current and patched are a high responsibility for everyone, and it's something every top executive should support."
So far, the main targets of the ransomware attack have been outside the United States. But neither the federal government nor U.S. corporations assume that this will continue to be the case.
Over the weekend, top security officials in the Trump administration, led by the homeland security adviser, Thomas Bossert, gathered in the White House Situation Room to assess the threat to U.S. interests, including government agencies, companies and hospitals.
Britain's defense minister, Michael Fallon, told the BBC on Sunday that the government was spending about $64 million to improve cybersecurity at the National Health Service, where many computers still run the outdated Windows XP software, which Microsoft had stopped supporting.
A government regulator warned the NHS last July that updating antiquated hardware and software was "a matter of urgency," and noted that one hospital had already had to pay about $900,000 to repair a breach that began after an employee clicked on a web link in an unsafe email.
The National Security Agency and the FBI are also working to find the people behind the malware attack.
Information for this article was contributed by Sylvia Hui, Christopher S. Rugaber, Brian Melley, Allen G. Breed and Anick Jesdanun of The Associated Press; by Jordan Robertson, Rebecca Penty, Stepan Kravchenko, Ksenia Galouchko, Robert Hutton, Jack Sidders, Adam Satariano, Nour Al Ali and Margaret Talev of Bloomberg News; and by David E. Sanger, Sewell Chan, Mark Scott, Motoko Rich, Keith Bradsher, Joe Cochrane, Steve Lohr, Austin Ramzy, Paul Mozur, Richard C. Paddock and Ceylan Yeginsu of The New York Times.
A Section on 05/15/2017